POST
Android Fingerprint Framework (1)
This page is trying to present a brief introduction on the android fingerprint framework, aimed at helping anyone who wants to learn android fingerprint-related knowledge, created by referring to some documents and android source code.
There are some articles throughout the internet to share android fingerprint-related knowledge. However, from my point of view, part of them are too complicated to understand and some aren’t very distinct. I wrote this article by referring to android source code and according to my personal working experiences, tried to make the contents simple and easy to understand.
From Android 6.0 (API23), android introduced a fingerprint API interface, that is FingerprintManager to support fingerprint identification. While at android 8.0 (API26), it is deprecated and replaced by BiometricPrompt API interface.
The below description is from the android official document about the fingerprint framework.
Architecture
The Fingerprint HAL interacts with the following components.
- BiometricManager interacts directly with an app in an app process. Each app has an instance of IBiometricsFingerprint.hal
- FingerprintService operates in the system process, which handles communication with fingerprint HAL.
- Fingerprint HAL is a C/C++ implementation of the IBiometricsFingerprint HIDL interface. This contains the vendor-specific library that communicates with the device-specific hardware.
- Keystore API and Keymaster components provide hardware-backed cryptography for secure key storage in a secure environment, such as the Trusted Execution Environment (TEE).
A vendor-specific HAL implementation must use the communication protocol required by a TEE. Raw images and processed fingerprint features must not be passed in untrusted memory. All such biometric data needs to be stored in secure hardware such as the TEE. Rooting must not be able to compromise biometric data.
FingerprintService and fingerprintd make calls through the Fingerprint HAL to the vendor-specific library to enroll fingerprints and perform other operations.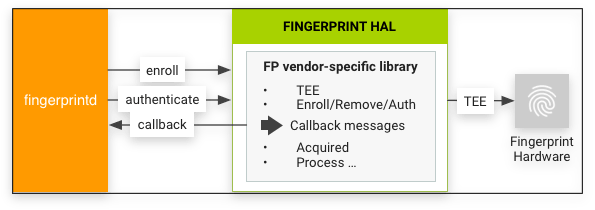
Implementation guidelines
The following Fingerprint HAL guidelines are designed to ensure that fingerprint data is not leaked and is removed when a user is removed from a device:
- Raw fingerprint data or derivatives (for example, templates) must never be accessible from outside the sensor driver or TEE. If the hardware supports a TEE, hardware access must be limited to the TEE and protected by an SELinux policy. The Serial Peripheral Interface (SPI) channel must be accessible only to the TEE and there must be an explicit SELinux policy on all device files.
- Fingerprint acquisition, enrollment, and recognition must occur inside the TEE.
- Only the encrypted form of the fingerprint data can be stored on the file system, even if the file system itself is encrypted.
- Fingerprint templates must be signed with a private, device-specific key. For Advanced Encryption Standard (AES), at a minimum, a template must be signed with the absolute file-system path, group, and finger ID such that template files are inoperable on another device or for anyone other than the user that enrolled them on the same device. For example, copying fingerprint data from a different user on the same device or another device must not work.
- Implementations must either use the file-system path provided by the setActiveGroup() function or provide a way to erase all user template data when the user is removed. It’s strongly recommended that fingerprint template files be stored as encrypted and stored in the path provided. If this is infeasible due to TEE storage requirements, the implementer must add hooks to ensure the removal of the data when the user is removed.
Working process
By referring to the official introduction, here I summarized the workflow according to my understanding.
- Android starts the fingerprint daemons process-
Fingerprintdduring boot up ininit.rc. - System server will start the fingerprint system service
Fingerprint Service. Fingerprint Servicecalls the interface ofFingerprintdto communicate with the fingerprint HAL code.- Fingerprint HAL interacts with the TA program and the latter undertakes the communication with fingerprint hardware through SPI.
- For the sake of security, the hardware SPI is mounted in the
TEEenvironment. The data collection of fingerprint images and the related processing of the algorithm are all carried out within theTEEenvironment. TheREEside only obtains the result of theTEEside.
In the next article, I will make a detailed introduction to the work process by inspecting the android source code.
To be continued…